Cyber Threat Life Cycle
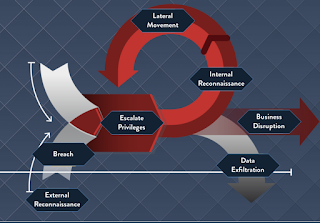
A Target threat is when attackers make a conscious effort to attack a particular organization. So they take their time to study the origination systems and strategically plan the attack. There several common steps that an attacker takes during a targeted threat. Several Steps in a Target Threat Life Cycle: External Reconnaissance occurs when attackers collect intelligence on HOW to successfully attack. The look for unpatched systems, ip address ranges, open ports and target endpoints. Breach (Penetration of the permitter) i s achieved using one of the many tactics used to gain access such as : social engineering , phishing, vishing, brute force attacks, tailgating, drive by download ect. Internal Reconnaissance is when the attackers collect intelligence on the internal system, by reviewing the system and search for admin accounts that they can hijack. Lateral Movement phase occurs when the attackers take control of the clients, servers, active directory domain con...
