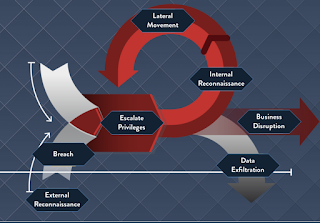
Labcorp suffers a data breach
Data breaches are happening more frequently than most companies are willing to admit. Labcorp, one the nation’s largest medical diagnostic companies, released a statement yesterday stating that it is investigating a possible Data breach that may have occurred over the weekend. I applaud Labcorp for coming forth so early in the breach response process. What sets a company apart from pack is not only their efforts to prevent and breaches, but how the structure their breach response polices. More than ever it is essential that effected parties are notified as soon as possible, to prevent further harm to the party and further reputational harm to the company. You can read more about the Labcorp data breach clicking the hyperlinked text.