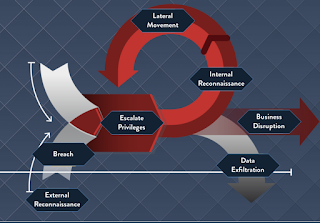
Cyber Threat Life Cycle
A Target threat is when attackers make a conscious effort to attack a particular organization. So they take their time to study the origination systems and strategically plan the attack. There several common steps that an attacker takes during a targeted threat.
Several Steps in a Target Threat Life Cycle:
- External Reconnaissance occurs when attackers collect intelligence on HOW to successfully attack. The look for unpatched systems, ip address ranges, open ports and target endpoints.
- Breach (Penetration of the permitter) is achieved using one of the many tactics used to gain access such as : social engineering, phishing, vishing, brute force attacks, tailgating, drive by download ect.
- Internal Reconnaissance is when the attackers collect intelligence on the internal system, by reviewing the system and search for admin accounts that they can hijack.
- Lateral Movement phase occurs when the attackers take control of the clients, servers, active directory domain controller.
- Target Attainment at this stage the attacker has a good handle on on IT systems and has installed the malware and gained access to several accounts, machines.
- Business Disruption, Exfiltration occurs when the attacker has achieved their end goal, which could be stealing data, corrupting systems or demanding ransom and disrupted business processes.
Businesses can mitigate the risks of a targeted threat by doing the following:
1. Assigning the least privileged access to users according to role based need.
2. Maintaining anti-virus software to detect normal threats.
3. Instituting threat monitoring software or system that can detect irregular user behavior and access permissions.
4. Have a threat response plan or protocol in place to proactively shut systems down in order to actively stop an attack.
5. Backup data in case a a breach results in data loss or denial, you can retrieve the data from a recent backup.
6. Make sure you have a breach response plan in order to get appropriate legal advice, notify the appropriate parties, remediate risks to stakeholders and patch up vulnerabilities.
Comments
Post a Comment
all comments to this blog are moderated